A part of FEV Group
Automotive Cybersecurity – Gap Analysis
Author -
Dr. Yuri Gil Dantas
Published -
Reading time -
3 mins
A part of FEV Group
Author -
Dr. Yuri Gil Dantas
Published -
Reading time -
3 mins
Cybersecurity has become a crucial discipline for the automotive domain. This is due to the introduction of advanced technologies such as connected systems, automated driving systems, and over-the-air updates. Additionally, with the introduction of cybersecurity regulations, particularly regulation UN R155 [1] and regulation UN R156 [2], cybersecurity has become mandatory for Original Equipment Manufacturers (OEMs). Suppliers are also affected by those regulations because OEMs often request their suppliers to follow the regulation’s requirements. Prior to market introduction, the OEM is required to successfully complete the homologation process, a stringent evaluation ensuring conformity with automotive standards and regulatory frameworks, such as those governing cybersecurity.
Conducting a cybersecurity gap analysis is crucial for identifying weaknesses before they escalate into critical issues – such as failing the homologation process. FEV provides comprehensive cybersecurity gap analysis services tailored to both OEMs and suppliers. By leveraging the insights from FEV’s analysis and implementing the recommended measures, customers can ensure their vehicles or components meet compliance standards, are fully prepared for homologation, and benefit from enhanced overall security, while avoiding costly delays.
The core of the cybersecurity gap analysis service is a systematic and comprehensive approach designed to provide clear insights into the current state of the automotive vehicle or components. Figure 1 illustrates the gap analysis approach, while its description is provided below:
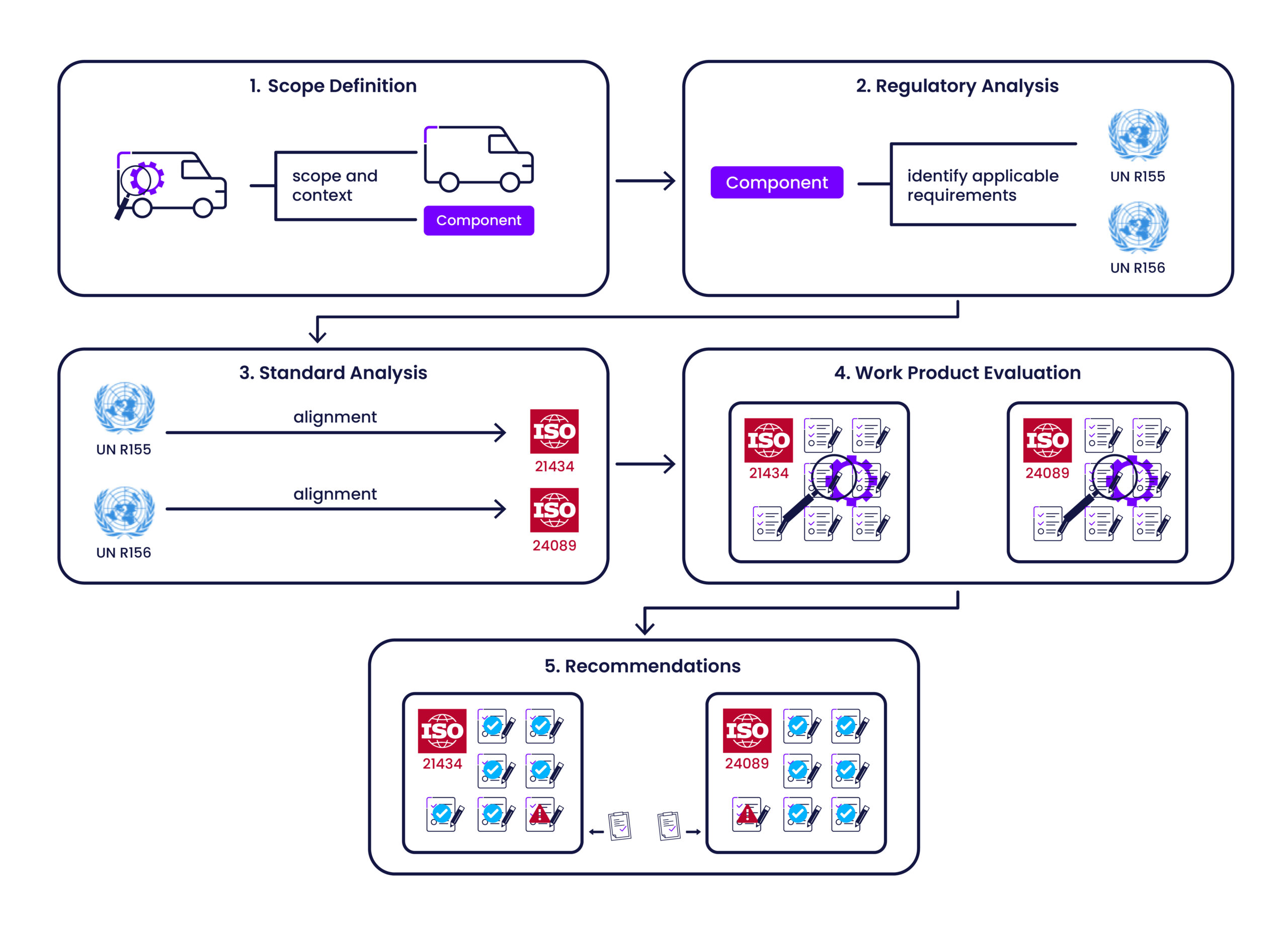
The benefits of the approach are clear: By systematically identifying and addressing cybersecurity gaps, OEMs and suppliers are assisted in reducing the risk of cybersecurity attacks and ensuring regulatory compliance. This not only protects the end-users of the vehicle or component but also helps OEMs and suppliers in achieving full compliance and protecting their own reputation.
If you are an OEM or a supplier seeking to ensure your vehicles or components meet the cybersecurity regulation requirements, our expert team is here to assist you. Contact us today for more details on how our systematic and comprehensive cybersecurity gap analysis can help you achieve full compliance.
[1] United Nations Economic Commission for Europe, “UN Regulation No. 155 – Cyber security and cyber security management”, https://unece.org/sites/default/files/2023-02/R155e%20%282%29.pdf, 4 March 2021.
[2] United Nations Economic Commission for Europe, “UN Regulation No. 156 – Software update and software update management system”, https://unece.org/sites/default/files/2024-03/R156e%20%282%29.pdf, 4 March 2021.