A part of FEV Group
Automation of Threat Analysis and Risk Assessment (TARA) using Artificial Intelligence
Author -
FEV.io
Published -
Reading time -
5 mins
A part of FEV Group
Author -
FEV.io
Published -
Reading time -
5 mins
The Threat Analysis and Risk Assessment (TARA) is a mandatory and essential work product of the cybersecurity lifecycle defined by the standard ISO/SAE 21434 for road vehicles.
Typically, TARA activities are performed manually by cybersecurity engineers – a time-consuming task that may result in incomplete or incorrect results. Furthermore, the task of performing TARA depends on the individual viewpoint of the respective cybersecurity engineer, which is to a certain degree subjective. As a result, TARAs performed by different engineers may vary significantly (Figure 1) potentially resulting in inconsistent results.
FEV has developed an AI based tool – TARA Copilot – to solve these shortcomings. FEV’s concept of the “TARA Copilot” is defined as a support for the cybersecurity engineer, who remains fully responsible and involved in providing the inputs for the automation routine and reviewing the results of every step performed by TARA Copilot.
This newsletter provides a high-level description of FEV TARA Copilot. Figure 2 depicts an overview of the architecture. It uses a modular, chain-based design to automate key TARA activities with the support of Large Language Models (LLMs). TARA Copilot automates the following activities: asset identification, damage scenario identification, impact rating, threat scenario identification, attack path analysis, and attack feasibility rating. Risk determination is performed deterministically, while risk treatment decisions remain project-specific and are therefore not currently automated by the tool.
Each TARA activity is encapsulated as an independent module within the chain, forming the backbone of the system’s modular architecture. Every module leverages LLMs to generate specific TARA outputs based on defined inputs – such as the item definition, tailored instructions (i.e., prompts) and, when required, external databases. The output of each module seamlessly feeds into the subsequent one; for example, the results from the asset identification are directly utilized in the damage scenario identification module.
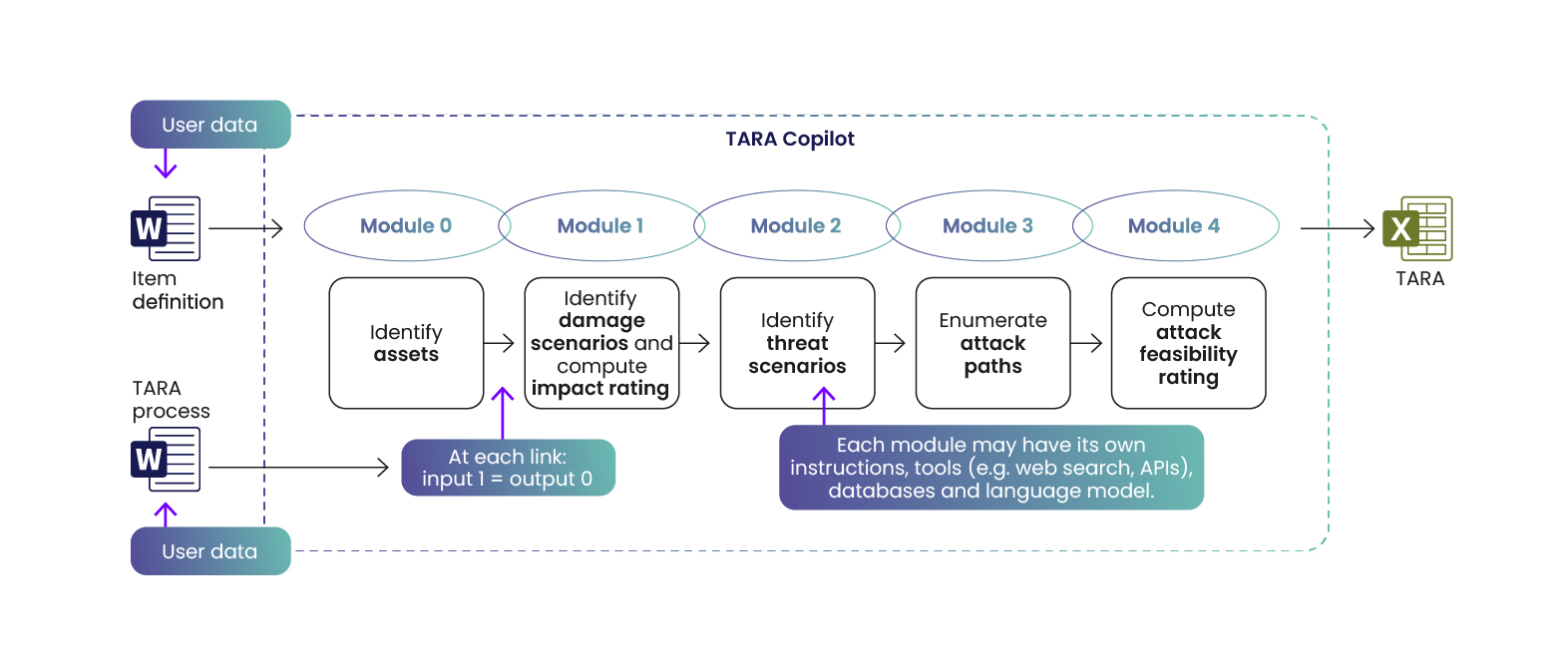
TARA Copilot allows users to start the process from any intermediate activity when the results of preceding activities are already available. For example, if asset identification has been completed and the assets are provided as input, TARA Copilot can begin directly with damage scenario identification. After completing all activities, TARA Copilot exports the results into FEV’s TARA report, enabling the responsible TARA owner to perform a systematic review. Review findings are transferred to updated inputs, and consecutive runs of TARA Copilot are conducted afterwards until the results are accepted by the TARA owner.
To provide insight into the tool’s decision-making approach, we briefly outline the rationale behind the identification of threat scenarios. FEV’s TARA process specification provides detailed definitions and descriptions of asset types (e.g., messages, software update), threat types (e.g., tampering), and attack surfaces (e.g., wireless access interface by an external actor). We systematically generated all possible combinations of asset types, threat types, and attack surfaces. LLMs were then used to validate which combinations correspond to threats from UNECE R155. For each valid combination, the LLM produced a detailed threat scenario description. An example of a valid combination and its corresponding threat scenario description is given below:
This approach is designed to meet UNECE R155 requirement 7.3.3(d), which states: “The vehicle manufacturer shall consider the risks related to all the threats referred to in Annex 5, Part A …” by ensuring that all relevant threats from UNECE R155 are evaluated by the tool.
FEV’s TARA Copilot has consistently demonstrated its effectiveness across a wide range of development projects, delivering measurable benefits in both efficiency and quality. Its integration into the TARA process has led to a remarkable reduction in overall effort – cutting the time required for finalization by approximately 50%. Beyond time savings, TARA Copilot significantly improves the quality and consistency of TARA results. Automated support ensures standardized output and reduces human error, while intelligent guidance helps teams maintain alignment with cybersecurity best practices. Thorough reviews by the responsible TARA owner as well as precise inputs for the tool – namely the item definition and the process instructions – remain essential for the quality of the TARA results.
We are currently collaborating with VicOne to extend TARA Copilot with continuous analysis capabilities that consider potential vulnerabilities in the item. To this end, VicOne’s xZETA product security platform and TARA Copilot are being integrated to create a dynamic, continuously updated TARA workflow. xZETA aggregates vulnerability data, including zero-day and undisclosed findings, and feeds this intelligence directly into TARA Copilot’s AI-assisted automation. The expected result is a responsive, adaptable framework that keeps cybersecurity strategies in sync with the changing threat landscape, enhancing efficiency, consistency, and response speed against newly discovered vulnerabilities.
TARA Copilot is now also available to external customers, offering a powerful solution for organizations seeking to enhance their cybersecurity risk analysis with greater speed, consistency, and confidence. Contact us to learn more about how TARA Copilot can support your organization: solutions@fev.io
Authors:
Yuri Gil Dantas, Bastian Holderbaum, Lars Kamphausen, Hendrik Ruppert