A part of FEV Group
How the secure Over-The-Air (SOTA) tool ensures cyber secure vehicle software updates
Author -
FEV.io
Published -
Reading time -
6 mins
A part of FEV Group
Author -
FEV.io
Published -
Reading time -
6 mins
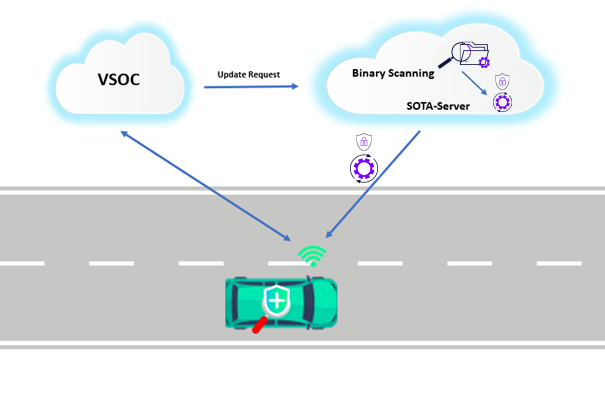
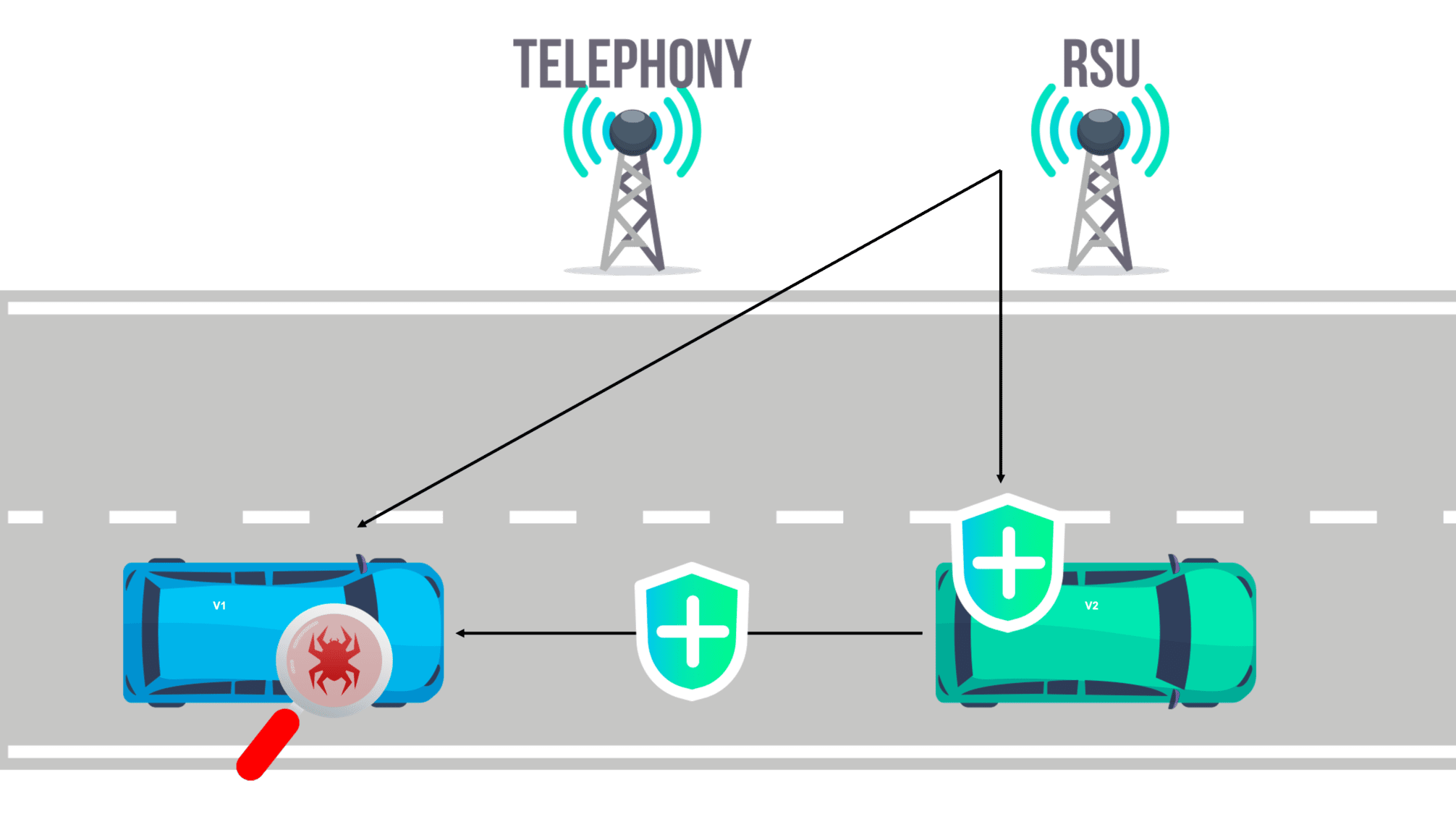
Imagine we have the following situation: the ego vehicle is driving on the road, the monitoring system on the vehicle in front has detected suspicious behaviour of its own and reported to the Roadside Unit (RSU). The RSU identified this abnormality as a vulnerability/bug for the software system, and it has been learnt that it is caused by a compromised or outdated software version. The remediation action of a software update is requested, and the surrounding vehicles, including the ego vehicle, have been informed.
This use case illustrates the need for vulnerability detection and providing software updates and security bugfixes via a secure update mechanism.
In this use case the software update is executed using the SOTA tool in the SELFY project. The primary aim of this tool is to provide secure and efficient delivery of software updates to the vehicle’s Electronic Control Units (ECUs) remotely.
This capability is crucial for maintaining or upgrading vehicle functionalities without the inconvenience of physical dealership visits. It ensures that the latest cybersecurity measures are implemented swiftly, addressing vulnerabilities, and enhancing the vehicle’s safety features. For the connected and automated vehicles, the OTA software update process will be highly significant in upcoming years and accelerate the upgrade of the vehicle software system, as in the mobile world.
Since the OTA update requires the access to the in-vehicle communication system and enables additional attack surfaces remotely to all the ECUs which have the OTA capability, the security of the update process itself is significantly critical. Due to its importance, the United Nations Economic Commission for Europe (UNECE) published in 2021 the regulation R156, requiring the vehicle type approval on the cybersecurity of the software update and the software update management system. In the SELFY project, the security of the OTA software update process is the focus.
The SELFY SOTA tool consists of its core part and integrated tools for facilitating a secure software update process.
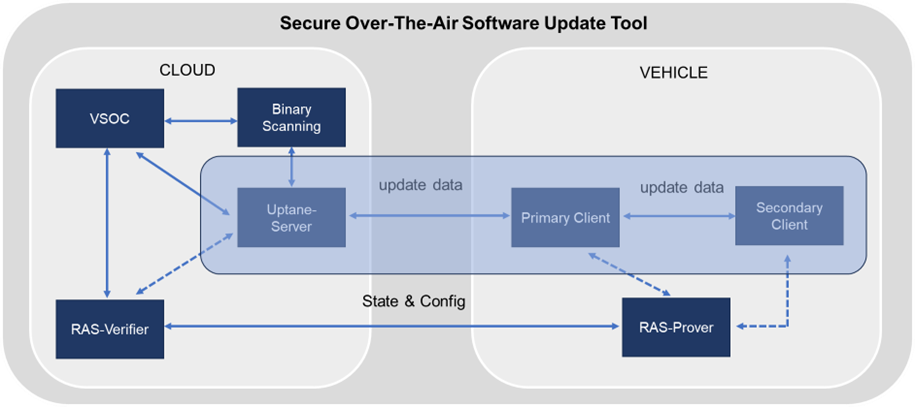
Based on the Uptane framework, the core of the SOTA tool includes the following components:
The SOTA tool works together with integrated tools for a secure update preparation and monitoring the secure process. These are:
The SOTA tool has the following main sequence of operations:

The SOTA server is implemented based on Uptane standard. Uptane is an open-source framework that ensures the security of software updates for vehicles. Uptane utilizes multiple servers, known as repositories, to provide security through the validation of images before downloading. The server-side implementation contains the following components:
In the vehicle side, there is a primary client, which relates to several secondary clients. In the first step of the update process, the primary client sends its vehicle version manifest to the Director repository. The manifest contains information about existing images.
Using this input, the Director chooses which images should be installed next. The images are then moved to the primary client, which will run a verification process. ECUs are generally classified in terms of access to storage space, memory, a power supply, and a direct internet connection. The form of verification that will be run –Full or Partial– is also based on the resources of the ECUs, as well as how security critical it may be. If the verification indicates no issues, the images can be downloaded to the secondary clients, and finally the software will be updated.

This research has been funded by the European Union, through the Horizon Europe research and innovation program, under grant agreement No. 101069748 – SELFY project. Views and opinions expressed are however those of the author(s) only and do not necessarily reflect those of the European Union or the European Climate, Infrastructure and Environment Executive Agency (CINEA). Neither the European Union nor the granting authority can be held responsible for them.